|
|
Just a week after code repository GitHub was knocked offline by the world's largest recorded distributed denial-of-service (DDoS) attack, the same technique has been used to direct an even bigger attack at an unnamed US service provider.
According to DDoS protection outfit Arbor Networks, that US service provider survived an attack that reached an unprecedented 1.7Tbps.
Last week Arbor, Cloudflare and Akamai reported an uptick in amplification attacks that abuse memcached servers to ramp up by traffic by a factor of 50,000.
Within a day of Cloudflare reporting that attackers were abusing open memcached servers to power DDoS attacks, GitHub was taken offline for about 10 minutes by an attack that peaked at 1.35Tbps.
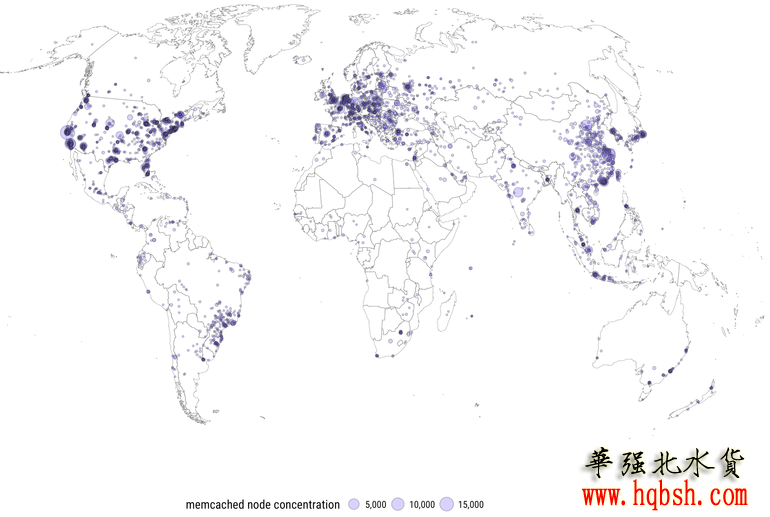
Memcached is a caching system to optimize websites that rely on external databases. Memcached-enabled servers shouldn't be left exposed to the internet, although at any given time over 100,000 are, according to Rapid7.
The attacks involve spoofing a target's IP address to the default UDP port on available memcached amplifiers, which return much larger responses to the target.
The attacks appear to be getting larger by the day. Before the attack on GitHub, Arbor Networks reported seeing attacks exceeding 500Gbps.
Arbor Networks' Carlos Morales predicts memcached attacks won't be going away any time soon because of the number of exposed memcached servers.
"While the internet community is coming together to shut down access to the many open memcached servers out there, the sheer number of servers running memcached openly will make this a lasting vulnerability that attackers will exploit," he wrote.
Morales' colleague, Roland Dobbins believes the memcached DDoS attacks were initially used exclusively by skilled attackers who launched attacks manually, but now they've been automated via rental 'booter' or 'stressor' botnets.
He notes that the potential for abusing memcached servers in application attacks was revealed by Chinese researchers in November 2017, but that as early as 2010 researchers had discovered widespread insecure memcached servers across the world.
As Ars Technica reports, some people attacking memcached servers are attaching a ransom note instructing targets to "Pay 50 XMR" or the equivalent of $18,415 to a specified wallet.
|
|
 |手机版|华强北商行
( 粤ICP备17062346号 )
|手机版|华强北商行
( 粤ICP备17062346号 )